The $2000 Bug: Explaining the Log4shell (Log4J) Vulnerability
Log4Shell (CVE-2021-44228) is a critical remote code execution (RCE) vulnerability in Apache Log4j 2, a widely used Java…
The $25,000 Bug: Explaining the React2shell Vulnerability
“React2Shell” is the name for the critical vulnerability CVE-2025-55182, which allows unauthenticated Remote Code Execution (RCE) in React…
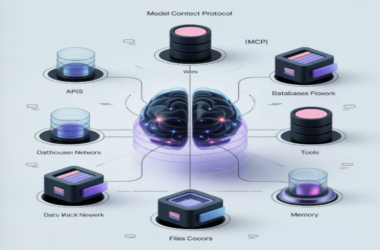
What Is Model Context Protocol? All You Need To Know
There’s no denying that AI is outpacing the development of the laws that regulate it, and that’s worrying…
AI in Cybersecurity: 5 Intelligent Tools Safeguarding Modern Businesses
Today, the increasing rate of new cyber threats keeps the digital world on its toes, especially AI in…
How to Install Cursor AI in Windows and Linux
Cursor AI is an advanced code editor. The AI capabilities of the code editor make it an effective…
How to Solve SQL Injection Vulnerability in WHERE Clause Allowing Retrieval of Hidden Data
SQL injection vulnerability (SQLi) remains one of the most dangerous web application. Among its many forms, injection through…
Real-World Impact: The Rise of Ransomware
In 2025, the rise of ransomware has become the digital equivalent of kidnapping only the hostages are databases,…
Inside the Mind Game: 5 Smart Social Engineering Tactics Redefining Cybercrime
In the field of cybercrime, the weakest link isn’t the software; it’s the user. In 2025, cybercriminals are…
How to Install n8n on Windows 11
n8n stands for nodemation, a mixture of node and automation. The 8 represents the eight letters in the…