In 2025, the rise of ransomware has become the digital equivalent of kidnapping only the hostages are databases, servers, and critical services. Unlike traditional data breaches that aim to steal information, ransomware attacks weaponize access itself. They exploit trust, time, and dependency.
Ransomware, once a nuisance for individual users, has evolved into a global economic and security crisis. Criminal groups now operate like startups running help desks, negotiating payment terms, and offering “discounts” to victims who pay quickly.
According to the FBI’s 2025 Internet Crime Report, ransomware losses surpassed $1.2 billion, nearly doubling in just two years. Behind those numbers are not just systems locked, but lives disrupted patients, students, and workers all frozen by a few lines of malicious code.
To understand how this menace keeps growing and what can realistically stop it we need to look deeper into its anatomy, its economic roots, and its real-world toll on people and institutions alike.
What Is Ransomware and Why It Keeps Rising
Ransomware is a type of malicious software designed to encrypt files or systems until the victim pays a ransom usually in cryptocurrency. Once the malware infiltrates a network, it locks critical data behind complex ransomware encryption, rendering it inaccessible. Victims then receive a digital ransom note demanding payment for the decryption key, often under tight deadlines and escalating threats. In many cases, even payment doesn’t guarantee recovery, as attackers sometimes vanish after receiving the money or leak sensitive data publicly.
Several key factors have accelerated this growth. The widespread adoption of remote work has expanded attack surfaces, giving cybercriminals more entry points through unsecured devices and personal networks. At the same time, many organizations continue to rely on outdated security frameworks or inconsistent backup practices, making recovery slow and expensive. Cryptocurrencies have further fueled the ecosystem, enabling untraceable transactions that embolden threat actors.
Don’t wait for the next alert, strengthen your defense today!
Ransomware isn’t just a headline it’s a global crisis reshaping the digital age. Awareness, vigilance, and preparation are your best shields in the age of ransomware.
Perhaps most importantly, ransomware thrives on psychology as much as technology. Attackers understand that panic is leverage locking systems that control hospitals, transportation, or municipal services forces organizations to act quickly, often choosing ransom payments over downtime.
How a Ransomware Attack Unfolds (Step by Step)
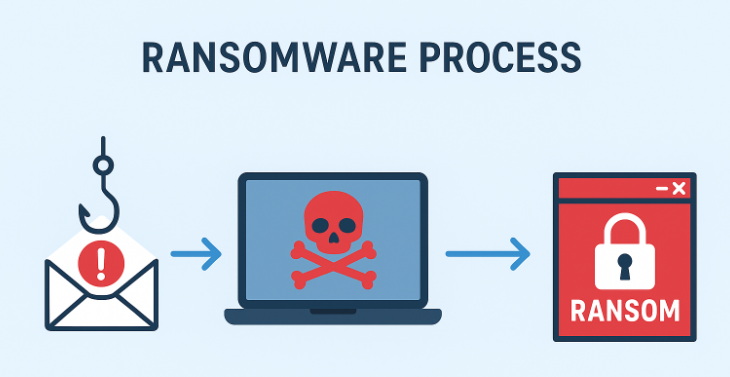
1. Reconnaissance and initial access
Attackers begin by learning the target like public web footprints, exposed services, leaked credentials, employee LinkedIn profiles, and third-party vendors. This reconnaissance is now often automated scanners and bots map internet-facing assets and enumerate weak RDP/VPN endpoints or unpatched services to exploit. Initial access commonly arrives via phishing, credential stuffing, compromised remote access, or exploitation of known vulnerabilities.
2. Foothold and reconnaissance inside the network
Once inside, attackers establish persistence and quietly expand their presence. This phase is methodical: planting web shells, creating backdoor accounts, or registering malicious services that survive reboots. They run internal reconnaissance enumerating domain controllers, mapping shares, and harvesting privileged accounts.
3. Credential theft and lateral movement
With credentials harvested, attackers escalate privileges and pivot laterally. Tactics include cracking password hashes, abusing misconfigured service accounts, and exploiting single-sign-on or poorly segmented environments. Lateral movement is frequently fast and surgical: attackers prioritize access to backup servers, file shares, and cloud storage that contain the “crown jewels.”
4. Data exfiltration
This creates leverage for “double extortion” attackers demand payment not only to decrypt files but to prevent public release of stolen data. Exfiltration can occur over encrypted tunnels, cloud storage uploads, or via staged hosts; the presence of outbound data flows that don’t match business patterns is a key detection signal.
5. Encryption
Ransom notes appear, often accompanied by a negotiation portal or clear instructions for payment (frequently demanding cryptocurrency). The speed of modern attacks means entire environments can be encrypted within hours; security teams describe a growing “ransomware speed crisis” where traditional response playbooks fail because attacker timelines have compressed dramatically.
6. Negotiation and post-payment risk
Following detonation, attackers may engage in negotiation, offering discounts or staged decryption. But payments carry no guarantee: decryptors can be faulty, keys may be withheld, and attackers may leak data regardless of payment. Moreover, paying can incentivize repeat targeting.
The Economic and Psychological Cost of Ransomware
The damage caused by ransomware extends far beyond the ransom demand itself. When an attack strikes, it triggers a chain reaction of financial losses, operational paralysis, and deep psychological strain across organizations and individuals alike.
However, the financial blow is only half the story. The psychological toll on victims especially small business owners and IT staff is often overlooked.
Get 20% off on your first hosting purchase. Provide everything you need to create your website.
Global Ransomware Incidents That Shook the World

Ransomware has evolved from isolated cybercrimes into global events capable of bringing entire nations and industries to a standstill. Each major attack over the past decade has rewritten cybersecurity history and exposing weak infrastructures. Here are the some real world ransomware examples:
“In more recent years, the Colonial Pipeline attack (2021) showed how ransomware could threaten not just companies but critical national infrastructure. A single compromised VPN account led to fuel shortages across the U.S. East Coast, sparking panic buying and emergency government response. The attackers, operating under the DarkSide group, reportedly collected a multimillion-dollar ransom before their operations were shut down“.
“Perhaps the most infamous example is WannaCry (2017), a worm driven ransomware that spread across more than 150 countries in just hours, crippling hospitals under the UK’s National Health Service (NHS), halting train systems, and forcing organizations worldwide to shut down operations. Its exploit a weaponized NSA vulnerability revealed how a single security gap could unleash chaos on a global scale. The estimated damages exceeded $4 billion, but the true cost was the loss of public trust in digital systems once considered secure”.
“Next came NotPetya (2017), often mistaken for a financial attack but later exposed as a politically motivated act of cyberwarfare. Its destructive payload wiped entire hard drives, targeting Ukrainian infrastructure and spilling into multinational companies like Maersk, FedEx, and Merck. The ripple effect was catastrophic logistics halted, shipping ports froze, and even global trade felt the impact. The attack cost over $10 billion, making it one of the most expensive cyber incidents in history”.
Each of these incidents underscores a harsh truth ransomware is no longer a question of “if,” but “when.” The attacks that once targeted individuals now hold entire economies hostage. And with every breach, the line between cybercrime and cyberwarfare continues to blur.
How Governments and Businesses Are Responding to the Ransomware Crisis
The response has evolved from paying ransoms in secrecy to forming global alliances, developing strict cybersecurity laws, and hardening defenses across every digital touchpoint.
Cyber Resilience
These directives required federal agencies and contractors to implement Zero Trust architectures, enhance incident response frameworks, and mandate rapid breach reporting. The message was clear cybersecurity is not just a tech problem but a civic responsibility.
Government Agencies
The Ransomware Task Force (RTF) a coalition of government agencies, cybersecurity firms, and NGOs was established to combat the growing threat ecosystem. Their work led to the “Counter Ransomware Initiative (CRI),” where more than 40 countries share intelligence, trace cryptocurrency payments, and disrupt ransomware supply chains. This marks one of the first unified global responses to digital extortion.
Cyber Insurance
On the business front, companies are moving from reactive to proactive strategies. Many are adopting cyber insurance not just as financial protection but as an enforcement tool for better security standards. Insurers now demand verified backups, regular patch management, and employee training.
Detection Systems
Moreover, private sector giants like Microsoft, Google, and IBM are investing billions in AI-driven threat detection systems that can identify and neutralize ransomware before it spreads. These systems rely on behavioral analytics rather than traditional signature-based models, enabling them to detect unknown strains in real time.
What Role Individuals Can Play in Combating Ransomware
hile governments and tech giants lead the macro fight against ransomware, the frontline defense begins much closer to home with the individual user.
Self awareness
For individuals, awareness is the first shield. Understanding that not every email attachment, update prompt, or social media message is trustworthy can stop an attack before it begins.The reality is that most ransomware attacks don’t start with complex code; they start with a single click on a malicious link, a weak password, or an unpatched system.
Multi Factor Authentication
Practicing digital hygiene using multi-factor authentication (MFA), keeping software updated, and backing up data offline turns every user into a line of defense. A vigilant employee who questions an unexpected file or login request can prevent a multimillion-dollar breach.
Technical Tools
Technical infrastructure also plays a vital role. Investing in network segmentation, immutable backups, and endpoint detection and response (EDR) tools ensures that even if one system is compromised, the infection can’t spread unchecked. Periodic vulnerability assessments, patching schedules, and the use of Zero Trust models can minimize exposure to emerging threats.
Conclusion
Ransomware has evolved beyond a criminal tactic it’s now a weapon of disruption in a world that runs on data. Every encrypted hard drive, every compromised hospital, and every halted supply chain tells a larger story about the fragility of our digital dependence. What began as isolated extortion attempts has matured into a global economy of cybercrime, where stolen credentials and malware kits are traded as easily as commodities.
But this rise also brings clarity. It reminds us that cybersecurity is not a luxury it’s a collective responsibility. Governments are enforcing stricter regulations, corporations are investing in layered defenses, and ordinary users are finally recognizing that a single careless click can spark a global crisis. The tide is slowly turning from reaction to resilience.
Every story we cover aims to decode complex attacks, highlight industry responses, and equip readers with the knowledge. Check out our guide about Social engineering tactics because awareness is the first step toward protection.
FAQ
What is ransomware and how does it work?
Ransomware is malicious software that encrypts a user’s files or systems, locking them until a ransom is paid. Attackers typically spread it through phishing emails, infected links, or software vulnerabilities.
Why has ransomware become such a big threat in 2025?
In 2025, ransomware is rising due to the expansion of ransomware-as-a-service (RaaS), weak cybersecurity in small businesses, and increased remote work all creating more attack surfaces for hackers.
What are the most famous ransomware attacks in history?
Major incidents like WannaCry, NotPetya, and the Colonial Pipeline attack exposed the global damage ransomware can cause, from halting hospitals to disrupting national infrastructure.
How can individuals and companies protect themselves from ransomware?
Use multi-factor authentication, keep systems updated, back up data offline, train employees on phishing awareness, and adopt a Zero Trust security model to limit ransomware exposure.
Should ransom payments ever be made to cybercriminals?
Cyber experts strongly advise against paying ransoms it encourages more attacks and doesn’t guarantee data recovery. Instead, report the incident to authorities and focus on restoring secure backups.